Blog
March 25 , 2024
5 min read
Urgent Threat Advisory : Ivanti Connect Secure VPN Vulnerabilities
5 min read

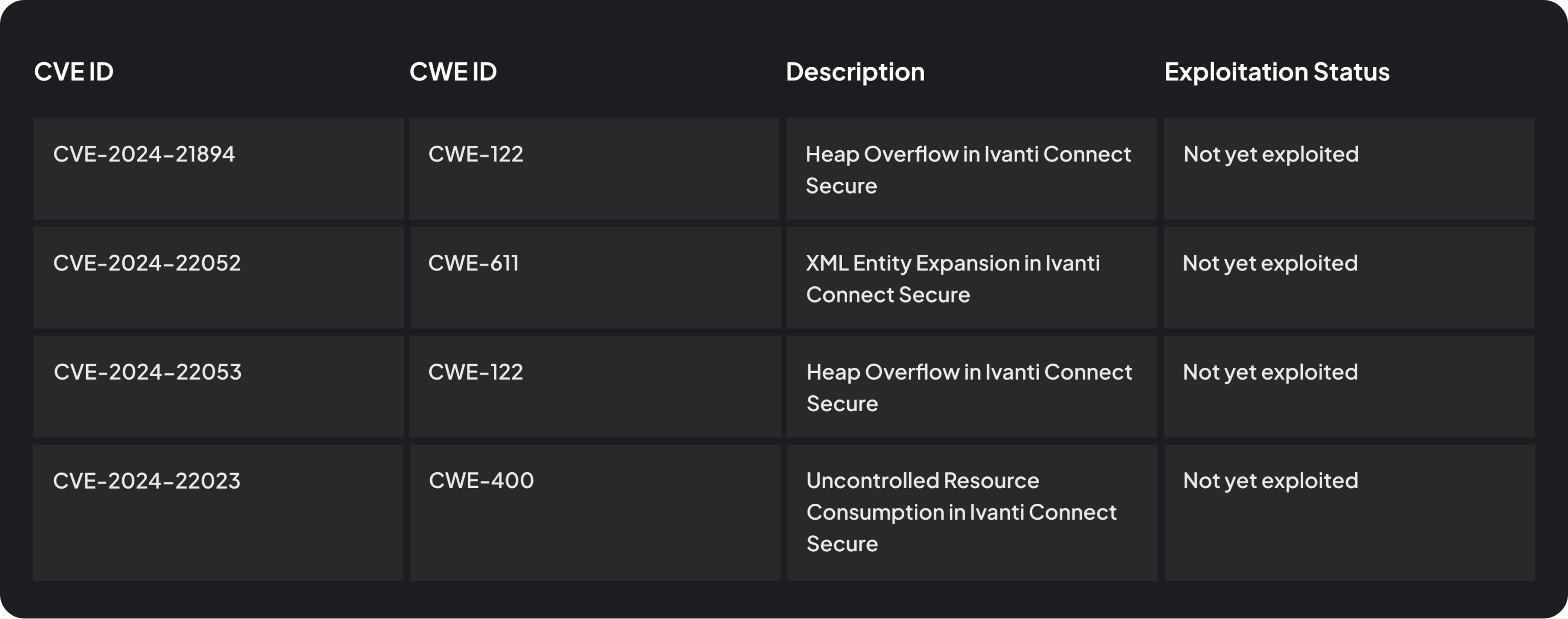
The RiskHorizon Threat Intelligence team has identified a critical trend that poses an imminent threat to organizations using Ivanti Connect Secure VPN. Four vulnerabilities, CVE-2024-21894, CVE-2024-22052, CVE-2024-22053, and CVE-2024-22023, have been disclosed. Historical exploitation, and common weaknesses shared in exploitation of Ivanti Connect Secure and other similar products suggests there is a high likelihood of a threat actor exploiting these new emerging CVEs within the next 7 days. This advisory provides an analysis of the threat landscape, historical exploits, and actionable recommendations to secure your network against potential attacks - before mass exploitation occurs.
Understanding the Threat Landscape
Ivanti Connect Secure VPN has been a frequent target of threat actors due to its susceptibility to exploitation. Reports from the Shadowserver Foundation suggest there are currently over 16,500 vulnerable instances worldwide, including 4,600 in the United States, the threat is substantial. These vulnerabilities, which include heap overflow and XML entity expansion, create opportunities for attackers to execute arbitrary code or launch disruptive Denial of Service (DoS) attacks, posing significant risks to organizational security.
Past incidents, such as the exploitation of CVE-2019-11510, can be used to inform current remediation efforts - our intent is not to predict similar exploitation by the same threat actors - but to highlight known tactics and threat actor motivations - to help you orient yourself to the threat landscape.
Threat actors, including nation-state groups like APT29 and UNC2452, and financially motivated actors have capitalized on previous Ivanti Connect Secure vulnerabilities. While ransomware/extortion incidents have been linked to recent Ivanti CVEs - like CVE-2023-35082, threat actors have typically target Ivanti Endpoint Manager Mobile (EPMM), and ransomware has not been attr
Mitigation Guidance
Our platform leverages our proprietary CORE (Cyber Optimized Research Engine), an AI-native functionality that assimilates millions of signals from across the deep and dark web. CORE provides unparalleled insights into emerging threats in real-time.
Mitigating the Risks
Mitigation Guidance
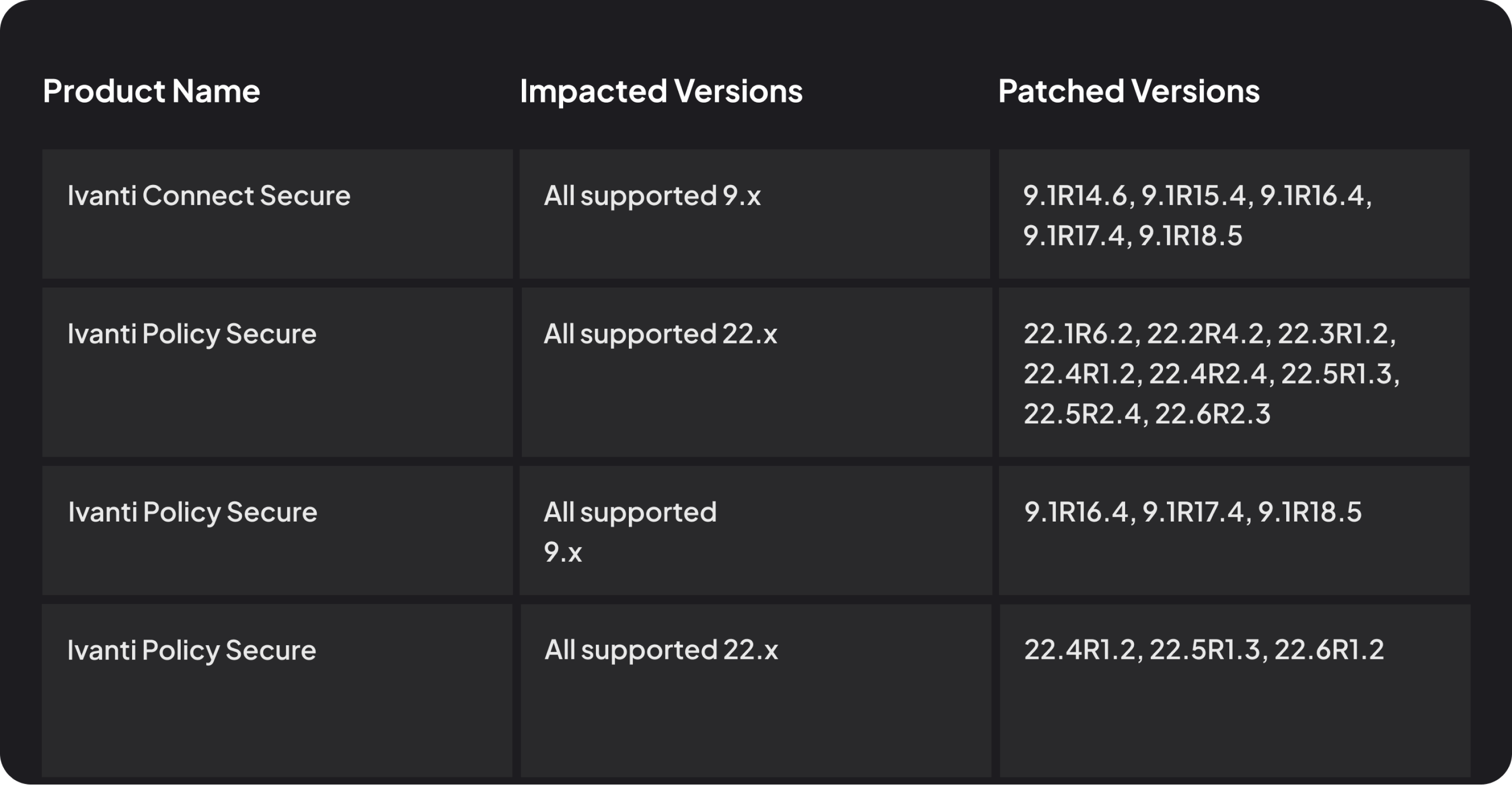
- Apply the available patches immediately to secure your Ivanti Connect Secure and Ivanti Policy Secure gateways.
- Use the updated External Integrity Checker Tool to verify the integrity of your Ivanti Connect Secure and Ivanti Policy Secure gateways after applying the patches.
- Refer to the KB article for detailed guidance on patching and using the Integrity Checker Tool.
- https://forums.ivanti.com/s/article/New-CVE-2024-21894-Heap-Overflow-CVE-2024-22052-Null-Pointer-Dereference-CVE-2024-22053-Heap-Overflow-and-CVE-2024-22023-XML-entity-expansion-or-XXE-for-Ivanti-Connect-Secure-and-Ivanti-Policy-Secure-Gateways?language=en_US
Why RiskHorizon?
RiskHorizon, our AI-native Continuous Threat Exposure Management platform, enables cybersecurity teams to take action within the critical window of time between threat discovery, discovery of impacted endpoints, and mitigation or remediation to stop a breach on impacted assets. Leveraging advanced AI algorithms, RiskHorizon predicts potential exploitation scenarios, enabling cybersecurity teams to take preemptive action against attacks.
RiskHorizon's multi-layered AI engine tirelessly scours the depths of the web, collecting and prioritizing millions of data artifacts to deliver actionable intelligence. Seamlessly integrating with existing security infrastructure, RiskHorizon centralizes threat data and accelerates decision-making processes.
Conclusion
In the face of imminent threats, proactive identification and mitigation of vulnerabilities are essential. The recent disclosure of critical vulnerabilities in Ivanti Connect Secure VPN serves as a call to action for organizations to fortify their defenses. With RiskHorizon by your side, you can navigate the complex cybersecurity landscape with confidence, thwarting attacks before they materialize and safeguarding your organization's assets.To learn more about how RiskHorizon can bolster your organization's defenses, visit RiskHorizon.ai.

Blog


