Blog
March 25 , 2024
5 min read
Understanding APT29: A Closer Look at the Cyber Threat Landscape
5 min read

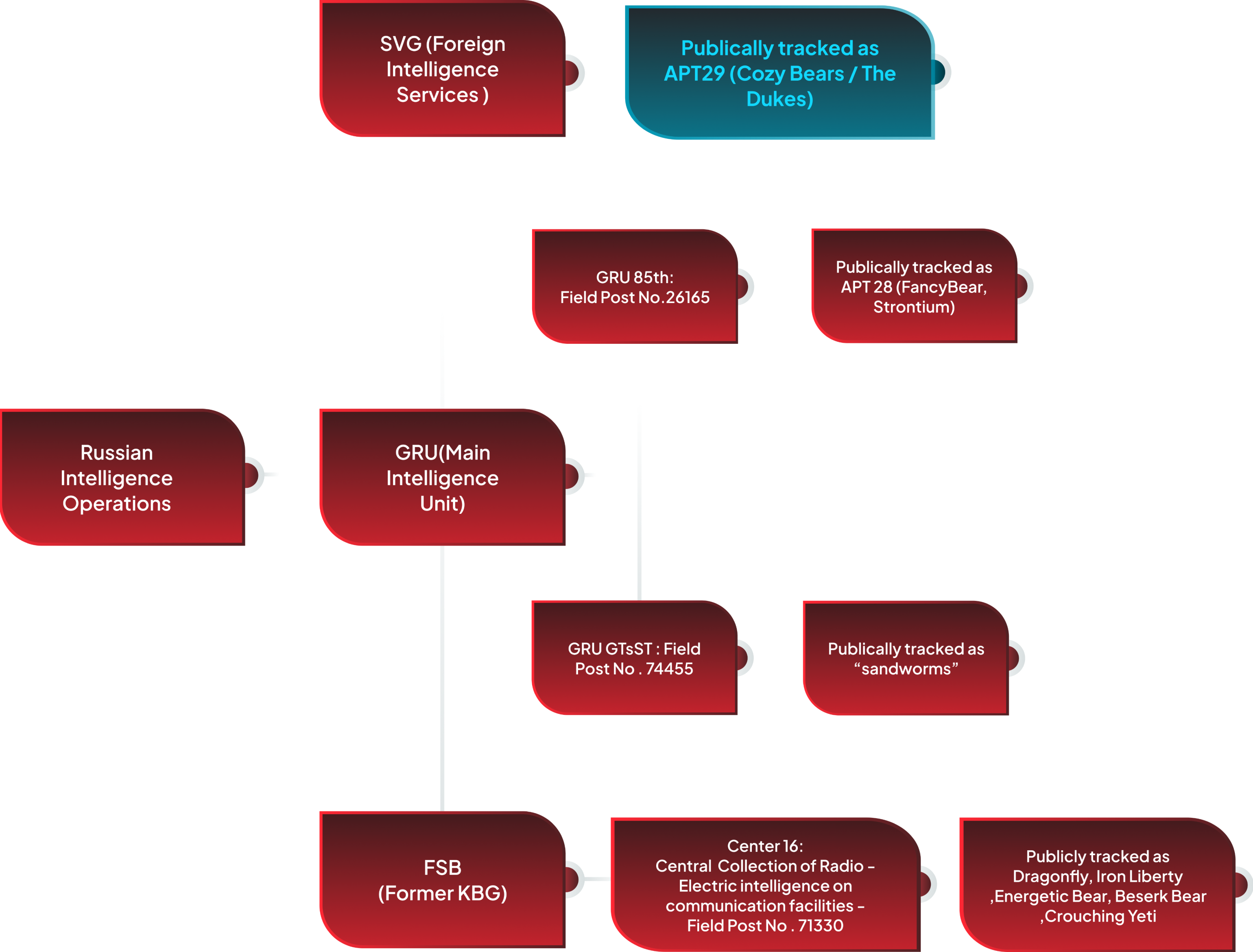
Recently, Microsoft disclosed a concerning security breach involving, APT 29, also known as Cozy Bear or Midnight Blizzards. This sophisticated group gained unauthorized access to a corporate Microsoft cloud tenant through a simple trick called a “Password Spraying Attack.”
Exploiting compromised credentials, they infiltrated high-level email accounts, including those of the executive team and the cybersecurity function, and stayed hidden for over two months.
This shows how sneaky and determined Advanced Persistent Threat 29 (APT29) can be. It is essential to learn about their tricks to stay safe in cybersecurity. Move further into the blog to understand this Threat Actor’s tactics and stay ahead of it
Known Exploited CVEs


Top Sectors Targeted by APT29
In 2023, Advanced Persistent Threat 29, a group linked to Russia’s SVR, targeted diplomatic and government sectors using tricky methods. They sent fake emails and even messed with a car ad in Kyiv, Ukraine. APT29 wanted people to download a photo album, but it was actually sneaky software. Diplomats are their main focus, and they use smart techniques to stay hidden. So, stay alert for APT29 tricks.
Top Malware Used
APT 29, a really tricky group, used powerful malware in big attacks. They started with SolarWinds, sneaking in through a backdoor called SUNBURST. Then they hit U.S. agencies and companies, like Homeland Security. APT29 keeps going, aiming at governments and even using special tricks on diplomats in Ukraine.
How To Mitigate Risks By APT29?
Enforcing a robust security posture is essential in mitigating risks posed by APT 29.

Organizations should implement MFA for access to sensitive resources to prevent unauthorized entry.

Move unsupported tenants into larger, managed environments for better monitoring and security.

Use VPN solutions and enforce conditional access policies to limit internet-based access to tenants.
With RiskHorizon’s features like Risk Posture Management, RiskTrends, RiskGPT, and AI RiskFeed, you can:

Gain visibility into emerging risks and shift security resources effectively.

Stay ahead of emerging threats with real-time vulnerability intelligence.

Predict, prevent, and detect threats with higher fidelity using AI fine-tuned for cybersecurity.

Stay informed with regular updates on cybersecurity trends, threats, and vulnerabilities.
- First Threat Actor Associated with CVE on2023-02-07
- First Ransomware Associated with CVE on2023-08-06
- CVE Published On2023-08-15
- First Malware Associated with CVE on2023-08-15
- CVE Published On NVD On2023-08-15
Combining these preventive measures with RiskHorizon’s features, businesses can proactively mitigate the risks imposed by Advanced Persistent Threat 29, ensuring a sturdy cybersecurity defense.

Blog


