Blog
March 25 , 2024
5 min read
Continuous Threat Exposure Management
5 min read

In an era where cyber threats are constantly evolving, a proactive approach to cybersecurity is not just advantageous; it's essential. Continuous Threat Exposure Management (CTEM), as outlined by Gartner, provides the strategic framework necessary for this proactive shift. It emphasizes the importance of ongoing vigilance — the identification, assessment, prioritization, and mitigation of security threats before they are exploited. Leading this proactive charge is RiskHorizon's Cyber Optimized Research Engine (CORE), an AI-driven powerhouse that is reshaping the cybersecurity landscape with its comprehensive CTEM capabilities.
Understanding CTEM
Scoping
Gartner defines the initial step towards CTEM as scoping your organization's attack surface—including entry points and assets, extending beyond traditional vulnerability management tools and programs. The identification of mission-critical assets is crucial in this step. RiskHorizon continuously maps your attack surface in real time to feed our discovery engine helping identify risks from an attacker perspective 24/7.
Discovery
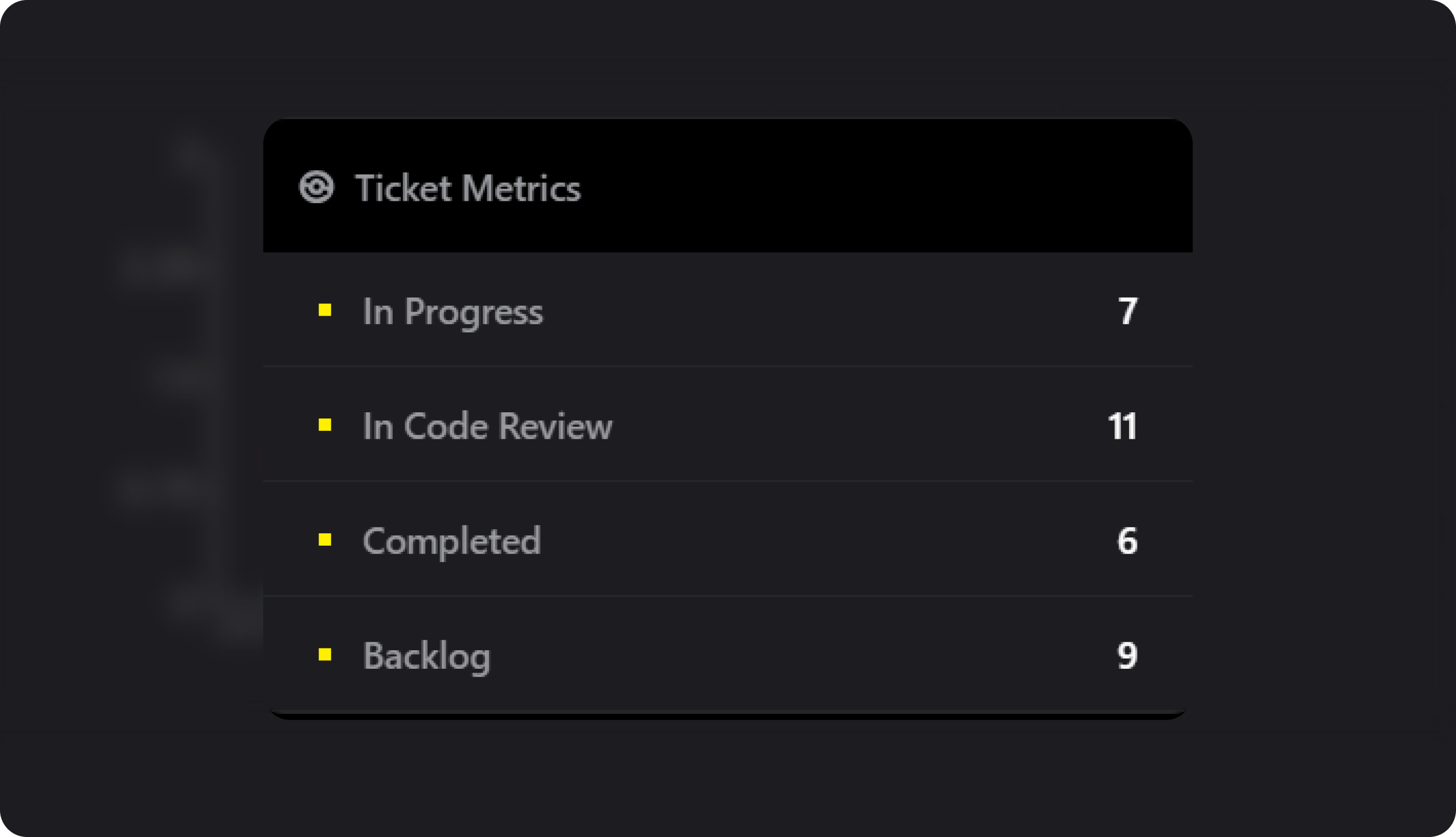
The discovery phase of CTEM involves the identification of misconfigurations and vulnerabilities. Combined with an understanding of the assets' criticality to the business, risk is better classified for prioritized remediation.
RiskHorizon empowers organizations to take control through continuous vulnerability scanning and attack surface mapping. Spot emerging risks sooner through the power of the CORE (Cyber Optimized Research Engine).
With the CORE, RiskHorizon provides real-time threat intelligence on emerging risks mapped to your evolving attack surface, helping you stay three steps ahead of threat actors.
Prioritization
Highlight (position off to the side): In 2023, 26,447 vulnerabilities were reported. Of those, only 200 had weaponized exploit code, and a mere 20 were observed in ransomware exploitation.
The objective of CTEM is not to address every issue but to prioritize, with context, the urgency with which an organization should respond to an emerging risk.
RiskHorizon CORE is an AI-native engine that identifies emerging risks in real-time by monitoring the deep and dark web, and prioritizes them based on the likelihood of impact or other emerging indicators such as weaponized exploit code, active exploitation, and tracks threat actor and malware associations.
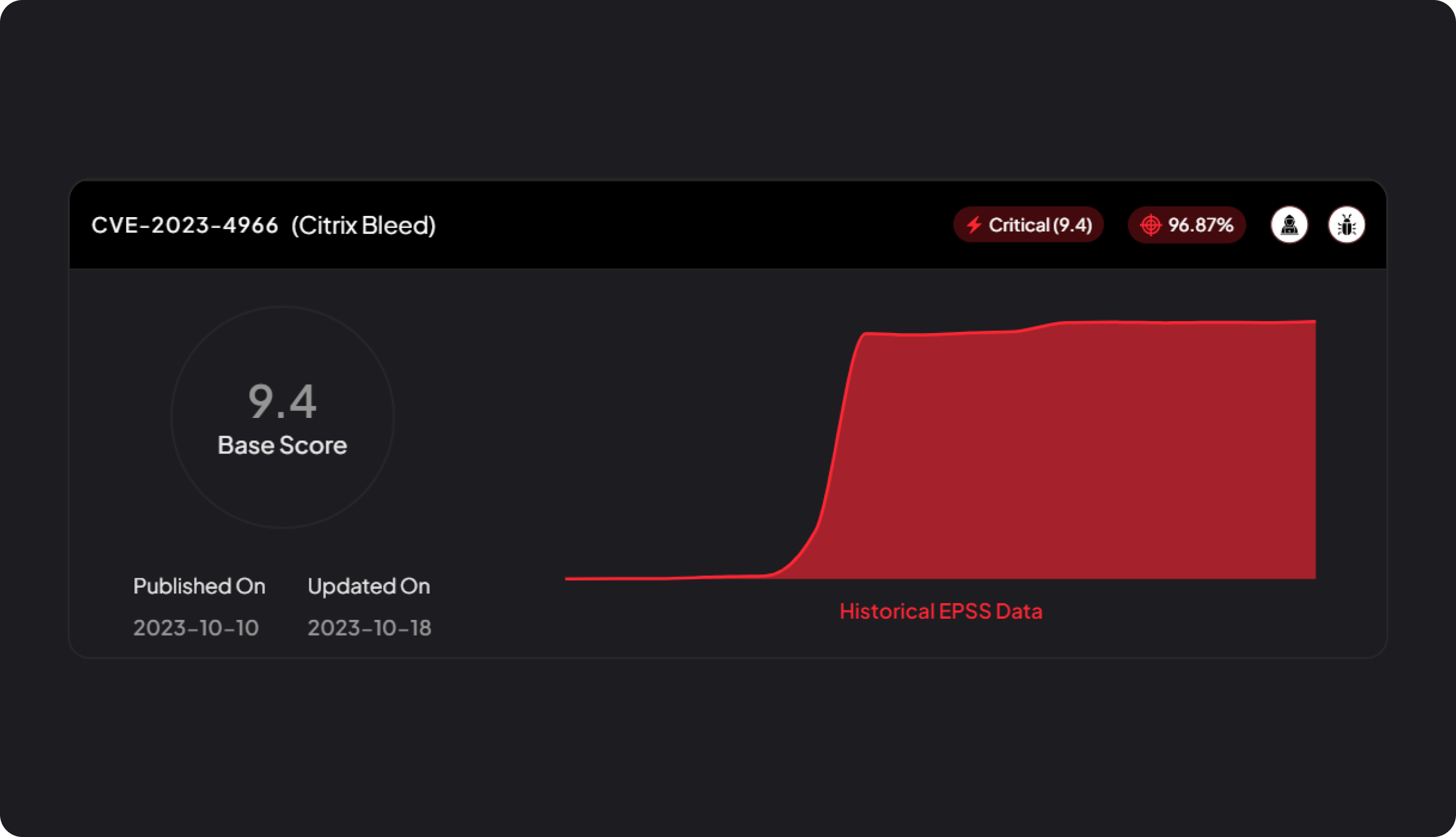
Validation
Triage risks in real-time with fully integrated access to emerging intelligence covering exploitation, ransomware, and threat actor attribution.
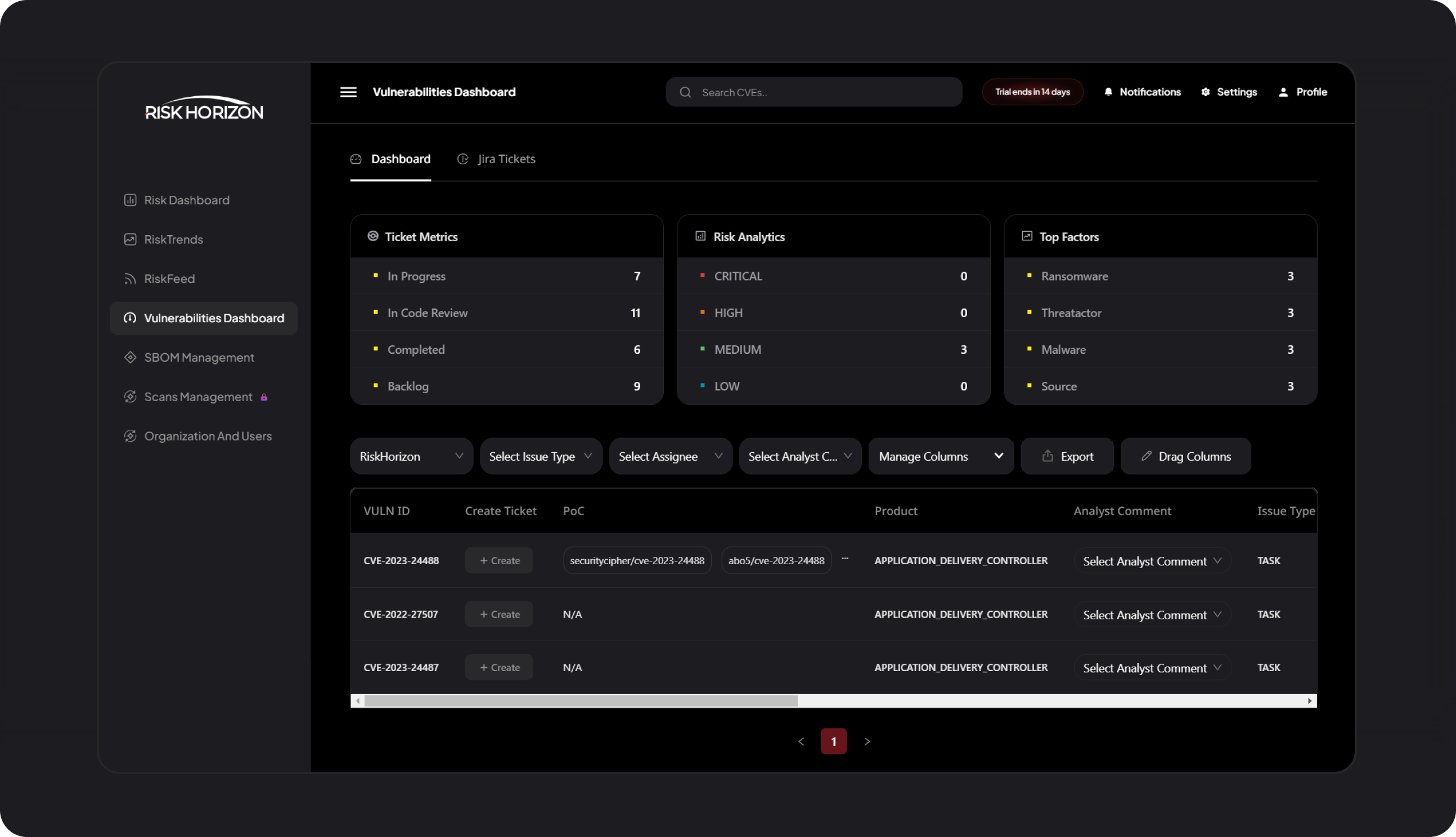
Mobilization
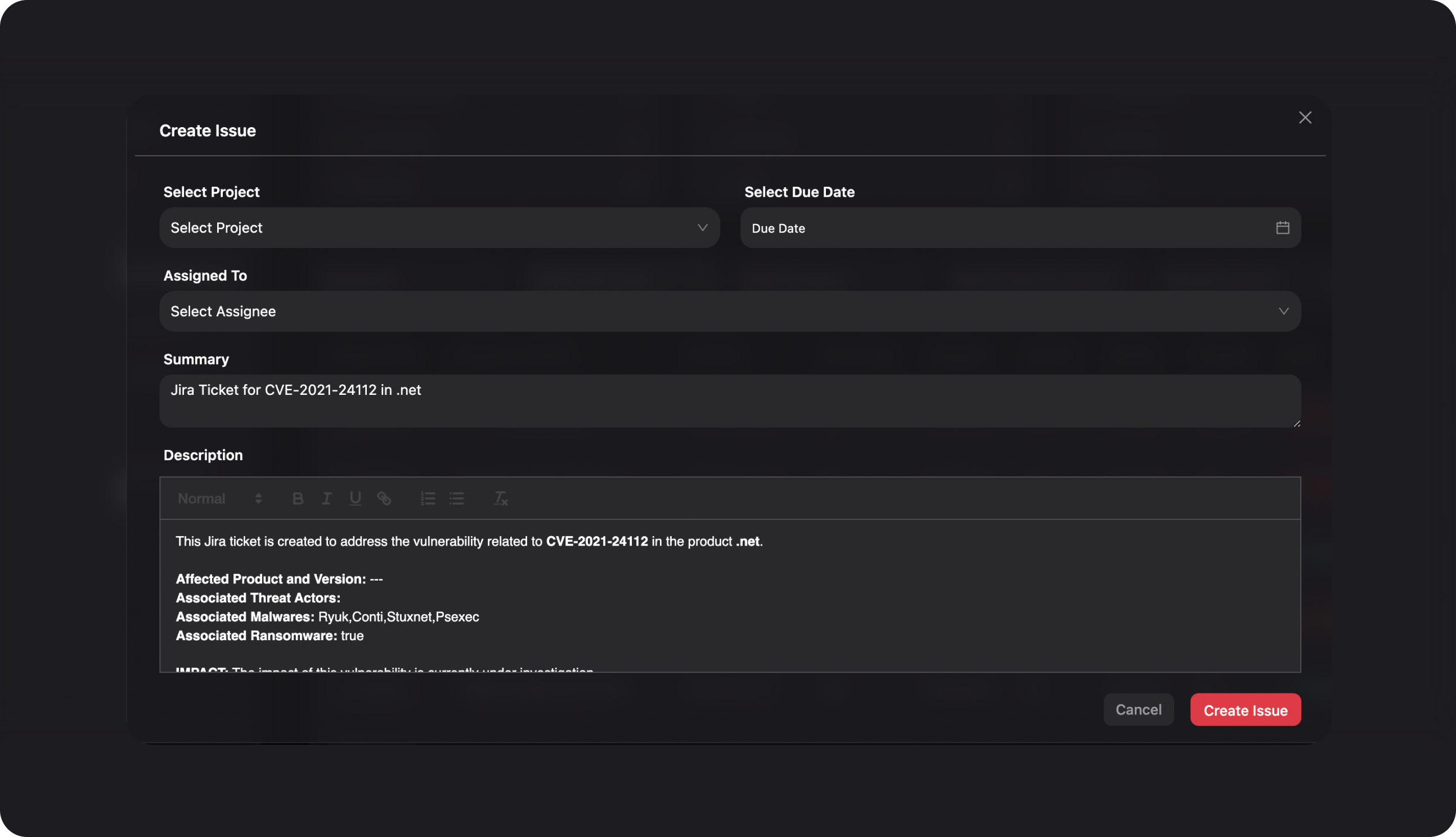
Assign validated vulnerabilities to product owners by creating tickets and tracking Jira updates on your Triage Dashboard in real-time . Stay updated on emerging risks through their lifecycle with real-time updates in Slack.
In conclusion, Continuous Threat Exposure Management (CTEM) is not just a strategic framework; it's a proactive approach to cybersecurity that every organization should adopt. With RiskHorizon's CORE, you can stay ahead of the curve, identify, prioritize, and mitigate threats before they become a problem. Don't wait for a breach to happen; take a proactive stance with CTEM and CORE.
Empower Your Security Strategy with RiskHorizon!
Take control of your attack surface, manage digital footprint expansion, and streamline threat targeting with fewer false positives. Take the next step!
Some of the things you may want to know
We answered questions so you don’t have to ask them.
What makes a cybersecurity due diligence assessment crucial in the context of mergers and acquisitions?
What are the elements of cyber security risk management?
What is the most famous risk management tool?

Blog


