See Threats. Stop Threats.
Automatically.
The only CTEM with built-in ADR. Evolve your threat posture without
adding yet another agent
Trusted by Industry Elite








Meet the Product
Gain continuous visibility into your exposures.
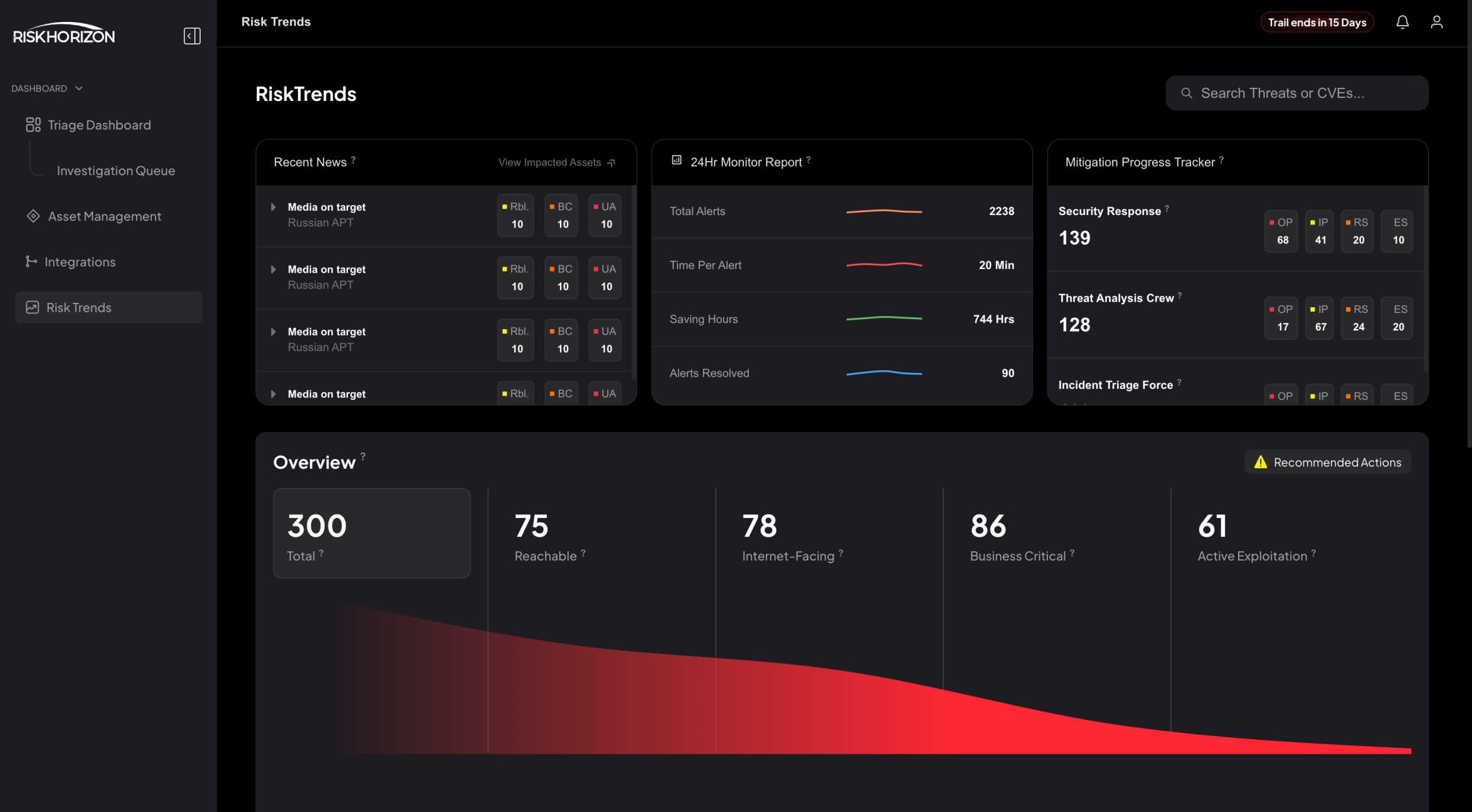
Triage Dashboard
Real-Time Insights and Prioritization for Efficient Incident Management
Investigation Queue
Centralized View to Track, Prioritize, and Manage Ongoing Investigations
Asset Management
Streamlined Oversight and Control of Organizational Assets in One Place
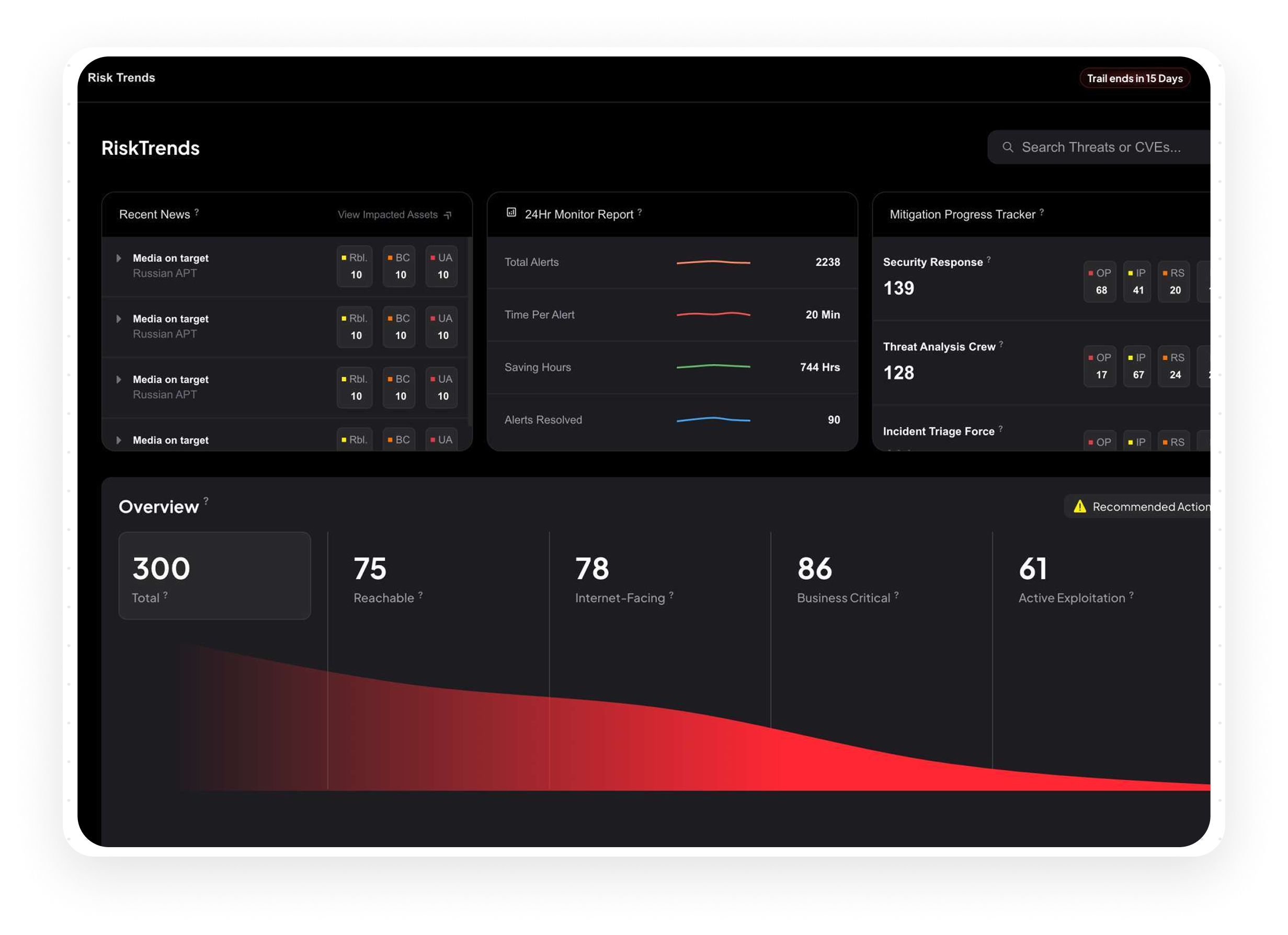
RiskTrends
Gain continuous visibility into your exposures
1%
Faster Remediation
4x
More Exploitable Threats Identified
200+
Integrations
The RiskHorizon Advantage
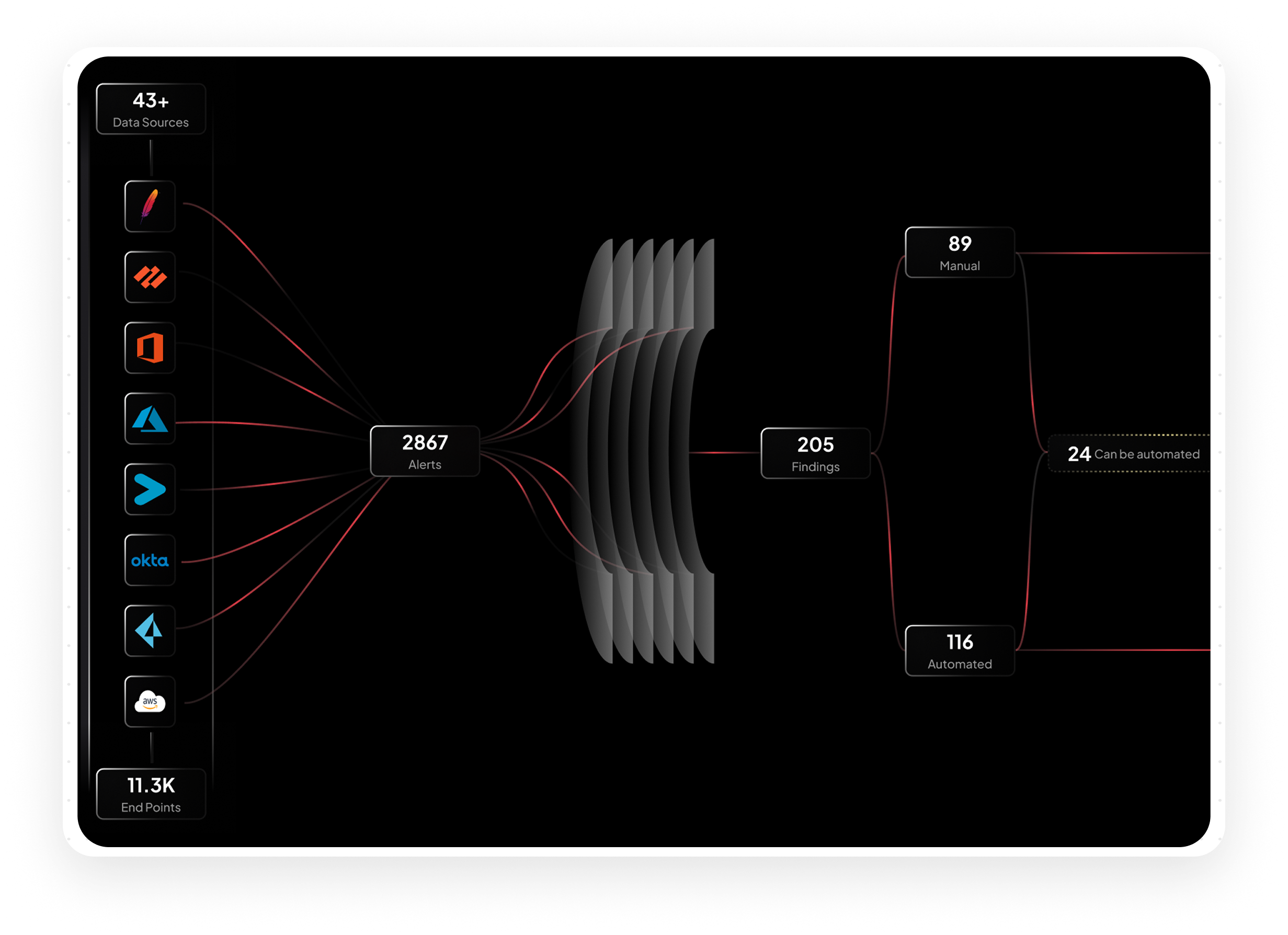
Centralize and Enrich
Cut the time to answer 'are we impacted' from days to minutes.

Gain continuous visibility into your exposures
unifying signals from 500+ tools like CrowdStrike and Wiz in real time.

Move beyond static risk scores
align security decisions with active attack campaigns, evolving threat actors, and real-time TTPs.

Prioritize and Orchestrate
Identify the threats that matter, when they matters, where they matter.

AI-driven prioritization cuts through the noise
mapping real-world attack campaigns to your actual security gaps.

Automated workflows enable immediate response in Slack
Jira, ServiceNow, and SIEMs. No more bottlenecks, no manual triage.
Detect and Respond
Stop attackers automatically using RunTime tracing, the next evolution in detection and response.

Not every exposure gets mitigated in time
Application Detection and Response (ADR) detects active exploitation in real-time.
Seamlessly integrates with EDR/XDR solutions
executing real-time containment of high-risk compromises.

Trusted by Industry Leaders
"RiskHorizon connects my business risk to our technical exposure. We can finally answer where we are most at risk in real time."
BISO, Fortune 100 Financial Services
"Our team used to waste hours chasing alerts. RiskHorizon helps us focus on what’s exploitable, impactful, and urgent."
AVP, Cybersecurity – Leading Healthcare System
"Tool sprawl and signal overload are killing security teams. RiskHorizon doesn’t replace our stack, it makes it work better together."
Former CISO, Fortune 100 Cybersecurity Vendor
"RiskHorizon tells me what’s real. Not theoretical vulnerabilities, but active threats and what they mean to our business and the context I need to confidently make the right decision."
Former NSA and Head of Threat Intelligence, Fortune 100 Financial Services
"With RiskHorizon our team can now triage faster and align issues to the right owners with less back-and-forth. It brought structure and clarity across the tools we already use."
VP of Security Operations, Large U.S. Healthcare Network
Recognized and trusted by industry leaders
Member of the NVIDIA Inception Program for our innovative approach to AI in cybersecurity.

